















Do you want to contribute by writing guest posts on this blog?
Please contact us and send us a resume of previous articles that you have written.
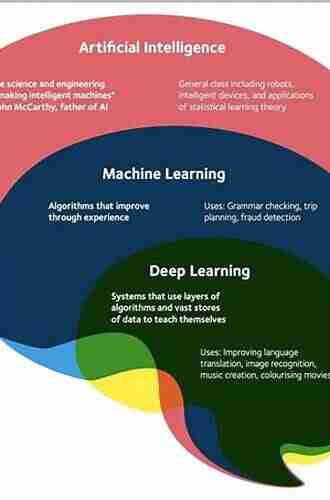
Network Anomaly Detection: Machine Learning Perspective

Are you aware of the hidden threats lurking in your network? With the increasing complexity of modern networks, it has become imperative to implement effective anomaly detection mechanisms. Machine learning, with its ability to analyze vast amounts of data and detect patterns, has emerged as a powerful tool in network security. In this article, we will delve into the world of network anomaly detection from a machine learning perspective.
What is Network Anomaly Detection?
Network Anomaly Detection refers to the process of identifying unusual or suspicious activities in a computer network. These anomalies could be caused by security breaches, system faults, or even the presence of malicious agents like hackers. By monitoring network traffic and analyzing patterns, anomaly detection systems can help identify and mitigate potential threats.
The Challenges of Network Anomaly Detection
Traditional rule-based methods for detecting anomalies in network traffic are often unable to keep pace with the evolving threats. Network operators are constantly faced with new attack vectors and sophisticated techniques employed by cybercriminals. This calls for more advanced solutions that can adapt and learn from new patterns.
5 out of 5
| Language | : | English |
| File size | : | 13420 KB |
| Print length | : | 366 pages |
| Screen Reader | : | Supported |
Machine learning algorithms offer a promising solution to this challenge. By training models on vast amounts of network data, these algorithms can learn to recognize normal network behavior and identify deviations from it. This adaptive nature of machine learning enables anomaly detection systems to evolve and improve their detection capabilities over time.
The Role of Machine Learning in Network Anomaly Detection
Machine learning algorithms play a crucial role in network anomaly detection. They provide the ability to analyze network traffic in real-time, identify abnormalities, and trigger appropriate actions. Let's explore some of the popular machine learning techniques used in network anomaly detection:
1. Unsupervised Learning
In unsupervised learning, anomalies are detected by comparing observed behavior against the expected normal behavior. This approach is useful when labeled training data is scarce or not available. Unsupervised learning techniques like clustering or autoencoders can identify patterns that deviate significantly from normal behavior.
2. Supervised Learning
In supervised learning, algorithms are trained on labeled examples to classify network traffic as either normal or anomalous. This method requires labeled training data that accurately represents different types of anomalies. Supervised learning algorithms like decision trees, random forests, or support vector machines can effectively classify network traffic based on learned patterns.
3. Deep Learning
Deep learning algorithms, such as convolutional neural networks (CNN) and recurrent neural networks (RNN),have shown great promise in anomaly detection. These algorithms can learn intricate patterns and relationships in network traffic data, allowing them to detect subtle anomalies that may go unnoticed by traditional methods.
4. Reinforcement Learning
Reinforcement learning can be used to train anomaly detection systems to take actions based on network observations and feedback. By providing rewards or penalties for certain actions, these systems can learn to make decisions that minimize potential risks. Reinforcement learning presents an exciting avenue for optimizing anomaly detection systems.
Benefits and Limitations
The integration of machine learning into network anomaly detection brings several benefits:
1. Enhanced Accuracy
Machine learning algorithms can analyze vast amounts of network data and detect anomalies with high accuracy. Their ability to learn and adapt to new patterns allows them to improve over time and stay effective against evolving threats.
2. Real-Time Detection
Machine learning algorithms can process network data in real-time, enabling timely identification and response to anomalies. This proactive approach helps minimize potential damages caused by security breaches.
3. Reduced False Positives
Traditional rule-based methods often generate a high number of false positives, leading to unnecessary alarms and wasted resources. Machine learning algorithms, by learning from training data, can minimize false positives and focus on true anomalies.
Despite these benefits, machine learning-based network anomaly detection also has its limitations:
1. Need for Training Data
Machine learning algorithms require substantial amounts of labeled training data to learn representations of normal and anomalous behaviors. Collecting and labeling this data can be time-consuming and resource-intensive.
2. Resource Intensiveness
Training and deploying machine learning models on large-scale networks can be computationally intensive. These algorithms may require significant computing resources, which can be a challenge for organizations with limited infrastructure.
3. Evading Adversarial Attacks
Adversarial attacks attempt to deceive machine learning models by injecting malicious samples that appear normal. Network anomaly detection systems based solely on machine learning may be vulnerable to such attacks, requiring additional defense mechanisms.
Network anomaly detection is a critical aspect of ensuring the security and integrity of modern computer networks. Machine learning techniques bring new possibilities for effectively identifying anomalies and mitigating potential risks. By leveraging the power of machine learning, network operators can enhance their ability to detect and respond to evolving threats. However, it is important to address the limitations of machine learning-based approaches and employ a comprehensive defense strategy that combines multiple methodologies.
5 out of 5
| Language | : | English |
| File size | : | 13420 KB |
| Print length | : | 366 pages |
| Screen Reader | : | Supported |
With the rapid rise in the ubiquity and sophistication of Internet technology and the accompanying growth in the number of network attacks, network intrusion detection has become increasingly important. Anomaly-based network intrusion detection refers to finding exceptional or nonconforming patterns in network traffic data compared to normal behavior. Finding these anomalies has extensive applications in areas such as cyber security, credit card and insurance fraud detection, and military surveillance for enemy activities. Network Anomaly Detection: A Machine Learning Perspective presents machine learning techniques in depth to help you more effectively detect and counter network intrusion.
In this book, you’ll learn about:
- Network anomalies and vulnerabilities at various layers
- The pros and cons of various machine learning techniques and algorithms
- A taxonomy of attacks based on their characteristics and behavior
- Feature selection algorithms
- How to assess the accuracy, performance, completeness, timeliness, stability, interoperability, reliability, and other dynamic aspects of a network anomaly detection system
- Practical tools for launching attacks, capturing packet or flow traffic, extracting features, detecting attacks, and evaluating detection performance
- Important unresolved issues and research challenges that need to be overcome to provide better protection for networks
Examining numerous attacks in detail, the authors look at the tools that intruders use and show how to use this knowledge to protect networks. The book also provides material for hands-on development, so that you can code on a testbed to implement detection methods toward the development of your own intrusion detection system. It offers a thorough to the state of the art in network anomaly detection using machine learning approaches and systems.

 Howard Powell
Howard PowellUnmasking the Enigma: A Colliding World of Bartleby and...
When it comes to classic literary works,...

 Jeffrey Cox
Jeffrey CoxCritical Digital Pedagogy Collection: Revolutionizing...
In today's rapidly evolving digital...

 Quincy Ward
Quincy WardThe Diary Of Cruise Ship Speaker: An Unforgettable...
Embark on an incredible...

 Derek Bell
Derek BellBest Rail Trails Illinois: Discover the Perfect Trails...
If you're an outdoor enthusiast looking...

 Adrian Ward
Adrian WardChild Exploitation: A Historical Overview And Present...
Child exploitation is a...

 Camden Mitchell
Camden MitchellThe Untold Story Of The 1909 Expedition To Find The...
Deep within the realms of legends and...

 Spencer Powell
Spencer PowellThrough The Looking Glass - A Wonderland Adventure
Lewis Carroll,...

 Sidney Cox
Sidney CoxAdvances In Food Producing Systems For Arid And Semiarid...
In the face of global warming and the...

 Art Mitchell
Art MitchellThe Devil Chaplain: Exploring the Intriguing Duality of...
When it comes to the relationship between...

 Edgar Hayes
Edgar HayesThe Mists of Time: Cassie and Mekore - Unraveling the...
Have you ever wondered what lies beyond...

 John Steinbeck
John SteinbeckOn Trend: The Business of Forecasting The Future
Do you ever wonder what the future holds?...

 Tim Reed
Tim ReedLove Hate Hotels Late Check Out
Have you ever experienced the joy of...
Light bulbAdvertise smarter! Our strategic ad space ensures maximum exposure. Reserve your spot today!

 Braden WardUnveiling the Fascinating World of Charles Dickens: A Pictorial Biography for...
Braden WardUnveiling the Fascinating World of Charles Dickens: A Pictorial Biography for...
 Robert Louis StevensonThe Ultimate Owner Manual For Keeping Parakeets: Pros, Cons, Care, Housing,...
Robert Louis StevensonThe Ultimate Owner Manual For Keeping Parakeets: Pros, Cons, Care, Housing,... Danny SimmonsFollow ·5.6k
Danny SimmonsFollow ·5.6k Alexander BlairFollow ·13.2k
Alexander BlairFollow ·13.2k Andy HayesFollow ·16.8k
Andy HayesFollow ·16.8k Dashawn HayesFollow ·19.4k
Dashawn HayesFollow ·19.4k Guy PowellFollow ·19.9k
Guy PowellFollow ·19.9k Jermaine PowellFollow ·8.5k
Jermaine PowellFollow ·8.5k George Bernard ShawFollow ·8.4k
George Bernard ShawFollow ·8.4k Emilio CoxFollow ·8k
Emilio CoxFollow ·8k